The KOSP wants to thank Erik Riedel of EMC for taking this on and EMC for providing a great facility for this event. Also a Special shout out and thanks to Erik’s team that facilitated everything!! You guys are awesome.
Goals
There was one primary goal:
- Demonstrate Drive, Enclosure and client Software interoperability. This would be accomplished via:
- Kinetic Drive Conformance Testing
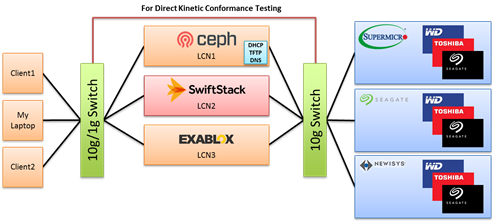
- Heterogeneous Client Software Configuration and demonstration, Proposed configuration is:
A secondary goal:
- Bring various stakeholders together to discuss issues that may hinder the adoption of open Kinetic based-technology.
 Equipment
Equipment
Drives
- Seagate 4T LombardKV
- Seagate 8T LamarKV
- Toshiba 8T IPHDD
- Toshiba 4T KVDrive
- WDC Wasp He8 micro-server with Kinetic application
Enclosures
- Newisys 4u 60 Drive EDA-4605
- Seagate 5u 84 Drive TitanKV
- Supermicro 1u 12 Drive K1048RT
Software
- Exablox OneBlox
- RedHat Ceph NuStore
- SwiftStack
Accomplishments
As a group we accomplished all of the goals set out:
- Interoperability. All three client applications were successfully configured with all 5 drives types across all 3 enclosures. We validated basic Puts, Gets and range operations. In some cases we validated batch operations as well.
- All drives went through the Kinetic conformance test suite. Although all drives had some issues they were minor and some were corrected.
Issues resolved on site
- WDC drive corrected conformance test issues
- Sanmina/WDC overcame enclosure I2C issues
- Toshiba IPHDD was modified to support 2.5gbps
- Redhat generated a new version of Ceph that supported all Kinetic drives
- Exablox worked around drives not yet supporting Announce protocol
- SwiftStack worked lab firewall settings to access its controller, after which it worked with all Kinetic drives in all enclosures
Press Release
It was agreed that promoting the general success of this plugfest via a press release would be beneficial to all. We will work with the Linux Foundation to create a press release memorializing the plugfest in a general fashion acceptable to all participants. It is expected to be completed sometime in January of 2016 due to the impending holidays.
Open Kinetic Discussions
- Management. One big topic of discussion was how we standardized on some of the basic management issues. Seagate proposed an intermediate step by having the enclosure vendors provide a script that enumerates the drive contents of an enclosure in a standard JSON format. However, through discussion it was decided that there needed a much more expanded view of this issue and that fitting into some existing standards such as RedFish might be appropriate. The issue is quite large as scaling of Kinetic devices may be on several orders of magnitude greater than existing servers scaling. Management will become a significant issue to Kinetic adoption.
It was suggested that a KOSP subcommittee be formed to drive this issue. AI: Philip to suggest to Governing Board the creation of this committee.
- Use of other open bodies. David Slik provided a presentation describing how we can split up some of the issues outside of the protocol and software and leverage other open groups to help resolve them. For example the Kinetic pinout and connector standardization have been driven by the SNIA Object Drive TWG and sent to SFF for standardization. Other Kinetic issues like enclosure management could be shared as well.
- Ordering Issues. This was specific protocol issue about the ordering requirements within a series of Kinetic operations. A Specification should be generated to nail down the exact ordering requirements across sync, async operations that occur within and across different connections. In addition the ordering within a batch should be exactly defined.
AI: Gary Ballance agreed to start the conversation on the members list by creating an initial straw man proposal.
- Certificate Issues. The X509 certificates on the drives, which are used for TLS based communication, need to be signed. How they are signed, by who and how they are managed is dependent on their use case. If the drives are on a relatively protected network and are merely using the certs for symmetric key exchange then Cert management is less interesting and probably not needed. If the drives are going to out in the wild on unprotected networks then the use of Certs for Identification and authentication comes into play. In this scenario Cert management becomes very important. Further discussions are required.
AI: Eric Dunn agreed to start the conversation with a problem description.
- CRC32/CRC64 Addition Proposal. Seagate originally implemented the CRC32 hash function in the kinetic protocol but in the drive and simulator used a CRC32C algorithm. Seagate wishes to fix this oversight by renaming CRC32 to CRC32C and adding CRC32 and CRC64 to the hash list in the protocol.
AI: TSC to take this up at the next meeting.
Next Meetings
It was agreed to aim at the next OCP Summit in San Carlos, CA on March 9-10 2016. We would try to provide a united demo at OCP Summit and possibly have one or two speaking engagements.
Attendees
35+ Attendees
11 Companies
AttendeeCompanyDan PollackAOLChristian BellefontaineEMCErik RieddelEMCJason ????EMCRizwan SheikhEMCFrank BarrusExabloxHuang ZhipengHuaweiJerry ChouHuaweiRobert QiuxinHuaweiDavid SlikNetwork ApplianceSage WeilRedhatSteve WakefieldRedhatJim BodwinSanmina/NewisysChiaming YangSeagateDavid BurksSeagateDuncan FurnessSeagateNicholas DanceSeagatePaul WoodsSeagateTim WalkerSeagateDon HeinsSeagate/DotHillAlbert ChenSwiftStackAbhijit DeodharToshibaEric DunnToshibaJohanna HernandezToshibaMark CarlsonToshibaPhilip KufeldtToshibaChistopher SquiresWDCCurt BrunerWDCGary BallanceWDCJosh JohnsonWDCMartin CzekalskiWDCNils LarsonWDCRob RyanWDC
